This is more of a note for myself. Hopefully it will end up in a search engine and I’ll be able to find my own solution when this happens again.
Yesterday, I went to post something to one of my blogs that I self-host on a Windows server. You’re on one of those blogs right now, go figure. And when I did, I got a very common error: 403 Forbidden when accessing the xmlrpc.php file. But, I had just successfully posted two days ago! What could have changed?
I connected to the server and updated the permissions on the folder, since that is usually what 403 means. That didn’t fix it. I did an IISRESET. That didn’t fix it. I did a full reboot. That didn’t fix it. I kept searching for information.
When you search for WordPress and xmlrpc, you get a crap-ton of results that warn of the dangers of leaving this file exposed. It’s a gateway for hackers!!!!!! It’s so hackable!!!!! Turn it off!!!! Disable any remote capabilities to WordPress!!!! These warning are geared toward users who use and reuse weak passwords. Of course there is authentication on anything xmlrpc does, so if you’re getting hacked, it’s your fault. Granted, there’s no protection from a hacker brute-forcing your xmlrpc URL until it finally hits something, but again, strong, unique passwords, people!
With that little rant out of the way, I do recognize the high sensitivity of this file. It would not be unlike me to take some extra precautions on it. And that’s exactly what I had done, and what I had forgotten I’d done.
I set up an IP address restriction on just that file, so only my home PC could access it. That makes sense since I only post using Live Writer from home. However, my IP address from my ISP changed in the last couple days and I didn’t notice. This is how I fixed it. If you instead want to use this info to secure your own WP site (and forget about it until your IP changes), go ahead.
In IIS, I navigated to the xmlrpc.php file in the content view
After highlighting the file, I right-clicked and chose Switch to Features View. You can see the specific file name is in the title. I chose IP Address Restrictions
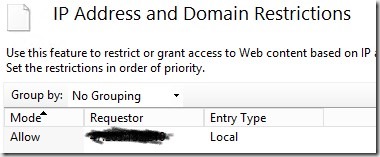
And in here is where I added/changed my home IP address. You can find yours at https://www.whatismyip.com.
And as you would expect, I am able to post to blogs again, as evidenced by this post right here.
